Thursday, November 02, 2006
As a Tehnical Writer I will
As a technical writer, I am responsible for communicating technical and business information to the reader that helps to understand and use the application. It is a craft through which information is delivered to those who need it. The word “Technical Writer” sounds new, but this profession was present long time back, where there was a need of interaction between human and application. Help or knowledge is required to get full advantage of the application, even the manuscripts from the medieval period could be looked upon as early technical writing. Over the years it has matured, and is still growing at an admirable manner. We understand reference and task-based information well enough that when we produce help files. Talking about a product development process, technical writing has not only been a part of the end user documentation, it has also assisted the organizations in the design and development process.
My inclination towards technology and software tools led me to love this technical writing job. This profession allows me to keep going with my passion of creativity. I would like to call myself as “Technical Communicator,” my work is an action oriented, expressing tasks precisely and clearly. Style guides and check lists help me to write correctly and concisely. I feel challenging and excited to find new dimension in defining my work. I interact with the team members to gather information about the usage, policies, and concept of the project and product. No doubt, I prepare documentation, but it is different from content writing, journalism, copy writing and others. I feel that technical writers must understand the product, project, technology, and business issues.
In the early days of my profession, I mostly used to write ‘User Guide,’ task involves screen-shots of application, drawing flowcharts, and step-by-step task completion procedure. Analyzing and running the application repeatedly some time led me to find bugs, which helped me to understand the application better. Afterward I also put my hand in web development, flowchart design, and image processing. I realized that lot of things has to be taken care in documentation, my technical background and my zeal to learn more helped me to venture into programming, often I get involved in application (software) form design, that’s what technical writers are different from other writers, we wears many hats in IT profession, one has to be versatile and their interpersonal skill is important for a team work.
I love critics, even document need testing. In editing process, I ensure consistency across each of the help files and controlling versions of the help as edits are made.
A software or hardware company had documents both for internal and external purpose. We all know how to use a mobile phone; still a manual comes with it. Study shows that 80% lifetime cost of the software is due to support and maintenance, which could be reduced through good documents. Companies are realizing the importance of documentation, however there are few formal education to to know or learn about technical writing, few communities are coming up to discuss and popularize it. As per Rahul Prabhakar it is right to say “Technical writing - the new black gold of India.” Let’s hope in the upcoming era of help we will revolutionize user-machine interaction through our active participation.
Thursday, October 05, 2006
King of Merchandise
What attracts is the look & feel of the product, and how handy it is.
For instance, see for luxury and accessory items like car, bike, mobile, television, and so on. Many people keep high-tech items with them without knowing its full usage of it. So, engineers are working to make their product user-friendly.
Take the case of Google, where 80% of the search is done. Yes, its technology is high, above that its interface (home page) is simple.
Every company has their standards or benchmarks to follow in their production house and customer know their brand style. Then what happens when a company acquires other one, they implement there, but that takes time. In cell phone arena, all brands has their own identity, interface is unique.
Many time product overlook some customers, product is customized for special class of customer like luxury car and economy car. But people get feel discriminated for difficulty in the application usage. In California, a federal district court judge ruled that a retailer may be sued if its website is inaccessible to the blind.
No matter what the product is, which ranges from accessories, hardware or software, at last it goes to the user, they are the ultimate to choose and use.
Wednesday, August 02, 2006
Product Usability
Here comes the usability and help into picture; no matter how robust the product is! If it can’t come-up with user’s expectations then it fails. But, there are exceptions where functionality and robustness of an application has to compromise with GUI, for example, mainframe application.
Saturday, January 28, 2006
Who is reading Help?
This question might come into our mind.
Marketing team will sell the products to the customers, and there will be more in the selling list. So, where these document into picture?
There is an influx of high-tech users, those who want the ultimate performance of their product. One day or the other you have to use a new product and to get guidance or training from other is not feasible every time. For instance, we get a manual with every purchase of a mobile. We all know how to make use of it, still manual gives details of every feature. Here comes User Guide or Manual, giving you minute detail of the product, you might not be reading the book from top to bottom, nor the help suggest to read in that manner, it will act as a quick help or reference guide to a problem. You might be categorized among the master of mobile user, but you may face problem in downloading audio song into your mobile, which is available in your mobile. Then you can quickly go through the TOC or index of your manual to know the correct procedure.
Now it has become a norm to provide user guide with every product, to familiarize and make it handy. Advantages of help with the product are as follows:
- Decrease training cost
- Naive user can work easily with the product
- Productivity increases
- Easy assistance available
- Popularity increases
Tuesday, January 10, 2006
ISMS Standards
This is not the first time BS7799 has been proposed as an ISO standard. The original version, BS7799:1995 was submitted in the summer of 1996 but was narrowly defeated. Those countries who voted in its favor were not dismayed, however. Australia and New Zealand for example recast it (by changing the UK legislative references to corresponding Australian and New Zealand references) and re-published it as AS/NZS 4444. The Netherlands embraced it wholesale and established a certification scheme, which went live early 1997. This international interest encouraged the British to develop the standard further. BS7799, How it works? Please note that ISO/IEC 17799:2005 just been published (15 June 2005). It replaces ISO/IEC 17799:2000. This means that Annex A of the current ISMS standard (BS7799-2:2002) is now out of date, as it refers to ISO/IEC 17799:2000. There will be an ISO/IEC version of BS7799-2:2002. It is anticipated that this will be published early next year and will be called ISO/IEC 27001. The Management Standard BS7799-2:2002 instructs you how to apply ISO/IEC 17799 and how to build, operate, maintain and improve an ISMS. The 1999 edition only instructed you to apply ISO/IEC 17799 and build an ISMS. The major components of an ISMS are summarized in Figure 1. The activities continually cycle around the PLAN-DO-CHECK-ACT cycle.
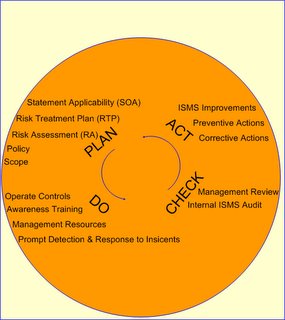
Figure1
The Code of Practice
ISO/IEC 17799:2005 defines 132 security controls structured under 11 major headings as follows:
- Security Policy
- Organizing Security
- Asset Management
- Human Resource Management
- Physical and Environmental Security
- Communication and Operation Management
- Access Control
- Information System Acquisition, development and maintenance
- Information Security Incident Management
- Business Continuity Management
- Compliance
These enable readers to identify the particular safeguards that are appropriate to their particular business or specific area of responsibility.
ISMS Standards Overview
The scope of any ISMS includes
1. People
2. Processes
3. IT systems
4. Policies
Concerns
- Confidentiality
- Integrity
- Availability
BS7799-2:2002 is a management standard, and explains how to build, maintain and improve an Information Security Management System (ISMS). It is predicated on risk assessment and the Plan-Do-Check-Act model, which are two vital ingredients of corporate governance. Thus, BS7799-2:2002 provides an excellent basis on which to build the management controls necessary to achieve an organization’s mission, to manage risk, to assure effective control and to seek improvements where appropriate. ISMS forms a part of an organization’s internal control system. The 7799 standards are particularly pertinent to corporate governance in an "e-biz" context, where risk management not only has to contend with the usual risks of doing business but also with rapidly changing IT/Internet risks and multiple legal jurisdictions. Thus the standards explain how to address the all-to-common and often devastating business impacts caused by viruses, web-site outages, improper disclosure of customer account details and incorrect pricing information. A growing number of politicians and leaders of industry are now recognizing the importance of these standards. Businesses, notably throughout Europe and Asia, who have a desire to flourish in the Information Age, are already taking advantage of ISO/IEC 17799.
Document and Data Control Procedure
- Information Security Manual
- Asset List/Risk Management Plan
- Statement of Applicability
- Guidelines
- Templates and Formats.
Goals of ISMS
Define and implement process and policies that protect our business assets and ensures efficient business operations and business continuity. Track and keep space with changing requirement of business and threat scenarios. Meet statutory requirements and implement security solution that are cost effective and that afford ease of use for meeting our information goal.
Security Policy
- Protect confidentiality, Integrity and availability of our business
- Meet contractual obligations on information security
- Meet regulatory and legislation requirements
- Ensure business continuity
- Undertake proactive actions and implement relevant information security policies to prevent security breaches
FAQ
1.What is ISMS ?
Information Security Management System, it mainly deals with protecting business assets.
What are business Assets ?
- Information. Database, System Documents, training materia, so on.
- Software. Developed and bought.
- Documents. Hard copy & softcopy, viz. Contracts, manuals, so on.
- People. Employees.
- Services – UPS, Power, so on
- Company Image and Reputation
What are the three concern properties of ISMS?
- Confidentiality. Ensuring that information is accessible to authorized access.
- Integrity. Safe guard the accuracy and completeness of information.
- Availability. Ensuring that authorized users have access to information.
Do you have internal audit?
Yes we have it once in every quarter
How is the audit conducted?
It is conducted by the Information Security officer. They investigate and recommend corrective ness/Preventive actions according to ISMS norms and close the same when they are resolved.
How do you protect sensitive data?
Any information that is considered sensitive will be password protected.
What is password policy?
- Every employee has to secure his password strictly, do not reveal it even to family member while working at home.
- Should not reveal it even to the CEO of the company.
- Password changes after every 45 days.
- Min length of password is of 8 Characters, with a combination of upper case, lower case and punctuation characters as well as letters.
- Should not have names like family members, pets, friends, coworkers, fantasy characters, computer terms, birth day.
What policies should not be violated?
- Copy Rights
- Trade secret
- Patents or Intellectual Properties
- Inappropriate licenses
Can we provide information to others outside company?
No, we should not provide information to other parties outside company.
What will you do when you find some sensitive documents in the office premises or some body violating the rules?
Inform it to the BCP (Business Continuity Plan) representatives of that month.
Are you permitted to bring outside material in the office premises?
No, you are not permitted to bring inside the office, we leave it at the security guard.
What will you do when fire breaks or there is an earth quack?
Don't panic; take proper steps to avoid calamities. Prepare yourself through mock-up drill.
What will you do when virus attacks your system?
We will first remove the network cable or shutdown the system and inform to the network administrator.
What is your asset Manager?
We maintain all the information in the VSS (Virtual Storage System) and access to VSS is given according to the need of the user.
What is HIPAA?
Health Insurance Portability and Accountability Act. Information should be protected as it deals with Health based information.
Were you given an induction, when you joined the company?
Yes.